You are an international company with multiple branches, suppliers, partners, and back offices in different countries. Your IT infrastructure is large: you maintain several data centres and outsource some functionality to the cloud.
Your offices exchange terabytes of data daily, but your various business applications require different traffic channel properties. Your video streaming depends on low latency, personal medical records demand secrecy, while the exchange of large files requires high throughput.
SD-WAN (Software-defined Wide Area Network) addresses this issue by connecting branches of your business through a virtual network. Every office is equipped with an edge node (a router) and all traffic passes through it. The edge node routes the traffic based on business requirements instead of IP addresses. This means that video conferences get the fastest channel, while the backup process uses the rest of the circuit or another cheaper circuit. A central controller manages the entire virtual network, and policy updates automatically spread across office branches. Businesses benefit in terms of security, time, and costs.
SD-WAN Today
While SD-WAN uses encrypted connections for every packet load, businesses can not control the path used by the data to travel from one router to another. Today`s internet consists of thousands of interconnected routers that belong to various internet service providers (ISPs). A data packet travels through dozens of routers before reaching its destination. Each router on the way receives a data packet and forwards it to the next “hop” based on its internal logic, much like playing a routing roulette. Thus, neither the sender nor the receiver controls the path of each data packet.
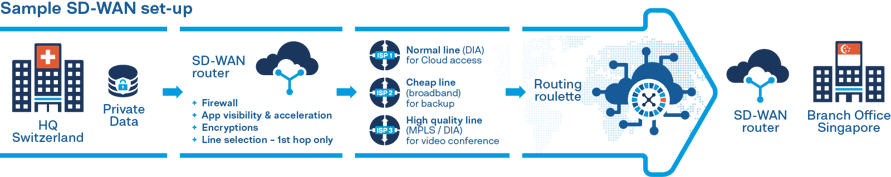 From an SD-WAN point of view, this particular end-to-end (E2E) path is not so important. The edge router in SD-WAN only controls the first hop of the data traffic, and for the remainder of the data`s journey, SD-WAN virtualises all underlying transport services and treats them as a single resource pool. Now, for various reasons, evaluating paths where data travels around the globe has become an essential procedure for businesses.
From an SD-WAN point of view, this particular end-to-end (E2E) path is not so important. The edge router in SD-WAN only controls the first hop of the data traffic, and for the remainder of the data`s journey, SD-WAN virtualises all underlying transport services and treats them as a single resource pool. Now, for various reasons, evaluating paths where data travels around the globe has become an essential procedure for businesses.
Some data must legally remain within a specific geographical jurisdiction, which means it is not allowed to pass through any external routers and needs to be treated as highly classified throughout its journey to its destination. For example, e-voting is an activity that requires a clear understanding of where requests are coming from and how a vote safely arrives on the government platform. The cleanest way to maintain data confidentiality and security is to control its path selection.
One step further, to guarantee performance, businesses need to control the entire end-to-end path. The performance of the data path depends on every single connection it passes through. Once a single connection is disrupted or a router is overwhelmed, latency or bandwidth of the data channel is impaired, affecting the speed at which data packets are transmitted.
Finally, routing on the internet is error-prone and not secure. The problem arises from how the internet handles data with the Border Gateway Protocol (BGP). BGP is the internet’s protocol that determines how data reaches a destination and the locations it passes through before. As the internet is constantly developing, new locations and connections emerge, adding to the possible paths data can travel. As the BGP selects based on efficiency, it will always choose the locations and paths that are most efficient to get to the data’s ultimate destination. This leaves the data at risk of passing through fraudulent locations that can intercept it and harvest information, otherwise known as BGP hijacking.
Malicious rerouting of the traffic, or BGP hijacking, occurs when a malicious router indicates that it can send data packets faster than other routers. Due to the nature of how BGP works, it will forward data through the malicious router, which in turn leaves it at risk. The BGP hijacker could steal credentials, eavesdrop or record the traffic, and then send the traffic to its final destination without the sender or receiver noticing the attack.
SCION - the groundbreaking new transport layer for SD-WAN
SCION addresses all these issues with the next generation internet. SCION provides a set of predefined path segments that the sender uses to construct an end-to-end (E2E) path. By giving the sender the ability to control the data traffic path, the sender can avoid specific ISPs or geographical locations, allowing for secure connections. In addition to security, SCION’s unprecedented level of flexibility leads to other integral advantages. Like SD-WAN, it can prioritize applications, allowing a network manager to choose a high-latency or cheaper path where necessary. SCION also enables managers to install closed and private circuits on the public internet and the simultaneous use of different paths.
The sender can choose different segments which have different properties. The sender has the flexibility to construct a tailor-made path for a mix of business requirements, whether they’re based on latency, bandwidth, geopolitical area avoidance, or a combination of all three. Paths are interchangeable, making SCION connections resilient to the failure of individual connections.
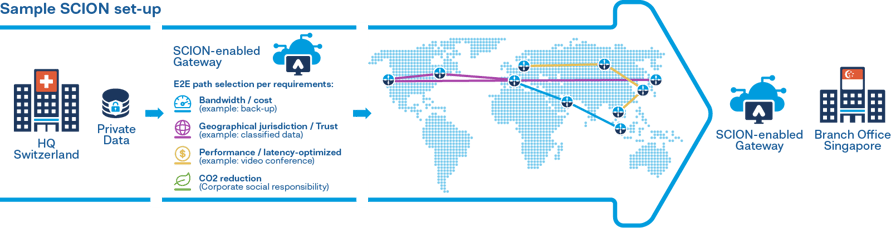
The SCION architecture, researched and developed at ETH Zürich for over a decade, delivers all the SD-WAN path selection features while guaranteeing the highest level of network security and reliability.
The full picture: SCION & SD-WAN
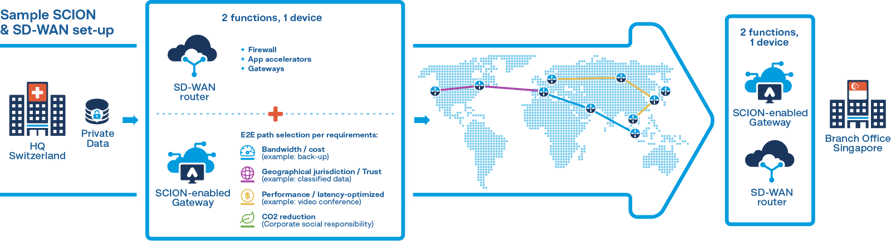
Today’s cybersecurity threats require a layered cybersecurity defense system. SCION is the crucial and fundamental network defense layer that can connect SD-WAN edge nodes in a more secure, reliable and transparent way. It brings advantages offered by SD-WAN into the DNA of tomorrow’s internet and makes virtual connections just as secure as leased lines while being more cost-effective. To sum up, SD-WAN users can benefit from SCION’s promise: speed, control, reach, and reliability.
Are you ready to complete your cyber defense fortress? Let's talk >

Thibaut Parmentier
Business Development Manager at Anapaya Systems AG









